Hola a tod@s!
En mi anterior artículo , vimos cómo extraer la shellcode de los “artefact” generados por Cobalt Strike. En este, veremos cómo con esa shellcode podemos sacar los datos de forma automatizada.
Recordemos que la información que nos interesa es:
- ¿ Es una shellcode de Cobalt Strike ?
- ¿ Hacia qué dirección ip o dominio se conecta ?
- ¿ A qué puerto ?
- ¿ Qué cabeceras añade, user-agent y otras ?
- ¿ La url ?
Dicho esto, pasemos a la acción.
¿ Os acordáis de aquel listado interminable de artefactos del artículo anterior ? Cojo uno al azar:
Son el mismo fichero. En el que, según habíamos visto, nos interesa esta parte:
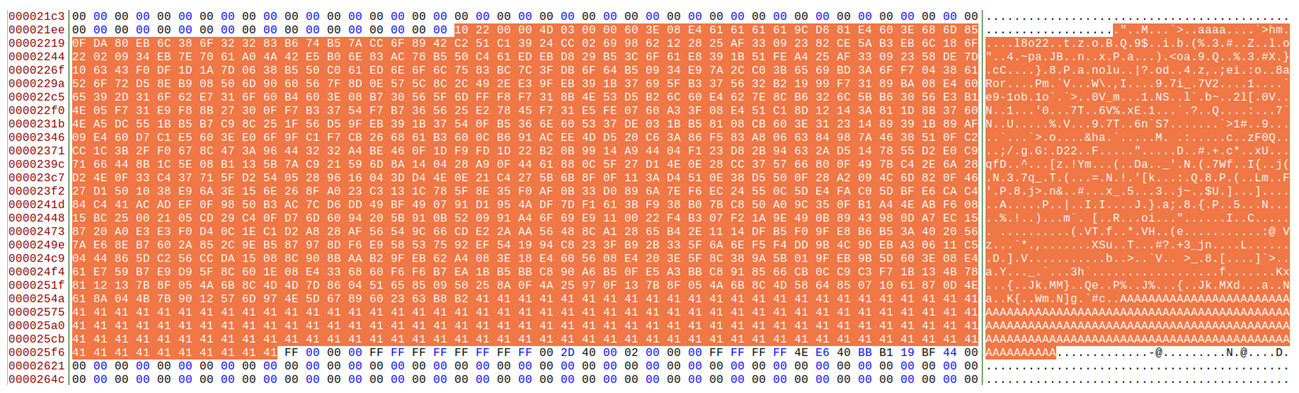
Para nuestro propósito, extraer esa zona, podría traducirse a algo como esto:
f = open(filename, "rb")
f.seek(0x2200)
shellcode = f.read(0x2600 - 0x2200)
f.close()
Abre el fichero “Artifact.exe”, posiciónate en 0x2200 y extrae esa zona que ocupa 1K. Algunas ser más grandes, ojo.
[0x004014b0]> ? 0x2600 - 0x2200
int32 1024
uint32 1024
hex 0x400
octal 02000
unit 1K
Ahora lo tengo que tratar, como binario y como un array de byte y pásale el algoritmo para descifrarlo.
data = bytearray(shellcode)
decoded = decode(data)
Supongamos que ya tenemos esa shellcode descifrada como sigue:
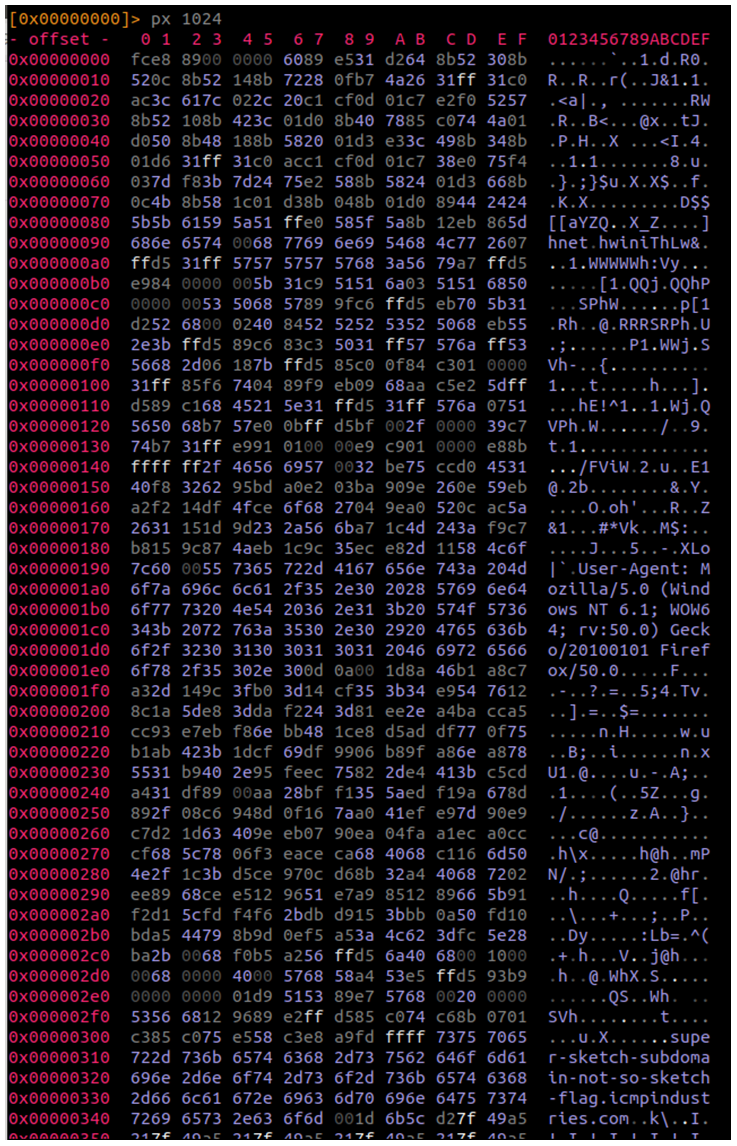
Al principio hice todo esto que veréis a continuación de otra forma pero daban resultados erróneos en shellcode con ciertos datos, ahora veis un user-agent, por ej. pero en otros casos la cabecera es mayor, se le añade el campo Host u otros campos, mirad un ejemplo:
Host: stackoverflow[.]com
Accept: */*
Accept-Language: en-US,en;q=0.5
X-Requested-With: XMLHTTPRequest
Etag: 4aeebe4a839401711e5daeaaa0fe85d5
Connection: close
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko)
Chrome/41.0
Así que me centraré en explicar lo más importante del script. Que por cierto, va dirigido para shellcode que realizan peticiones http(s).
Aunque el script funciona con shellcodes de 64 bits, en el artículo explico las de 32, que son las más peculiares. Hay que comprobar paso a paso si se trata de este tipo del shellcode ya que en caso contrario no tiene sentido sacar ip, dominios, user-agents, etc. Así que vamos comprobando paso a paso.
Lo primero si pertenecen a Cobalt Strike. Deberían comenzar siempre de la misma forma, ¿verdad?
Shellcode x32:
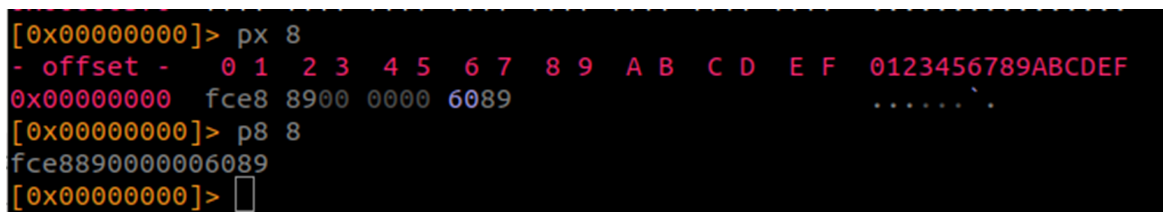
Shellcode x64:
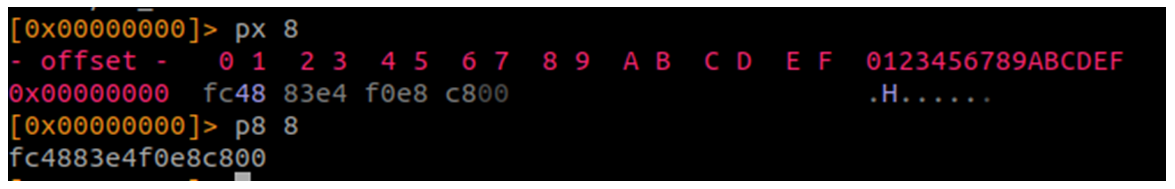
Esa debería ser nuestra primera comprobación. Pero… nos pasaría esto, así que no seamos tan estrictos.
La siguiente comprobación que debemos realizar es esta:
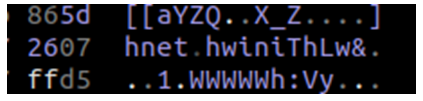
Si recordáis el uso de Scdbg, muy útil para estos casos, veíais algo como esto:
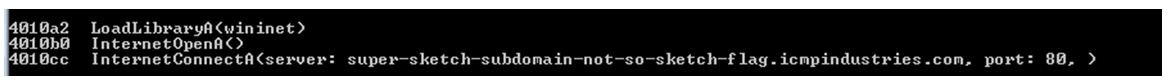
Busco esas cadenas:
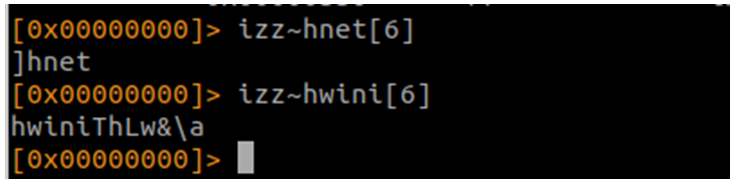
Busco el User-Agent:
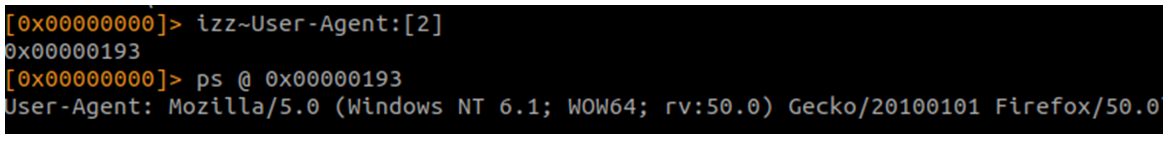
Busco el puerto:
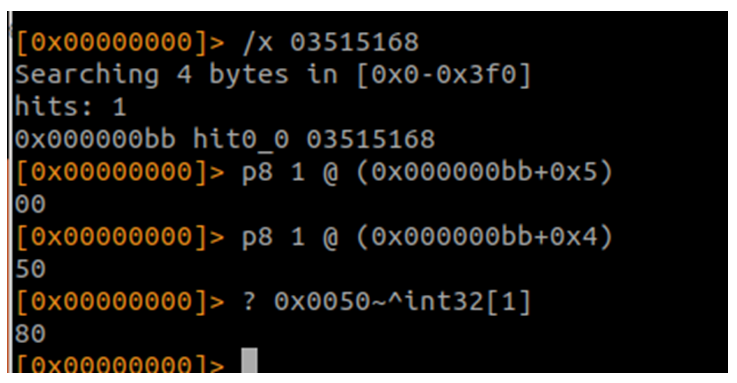
Está en little endian, así que lo necesito al revés.
Calculo la ip o dominio (dominio en este caso):
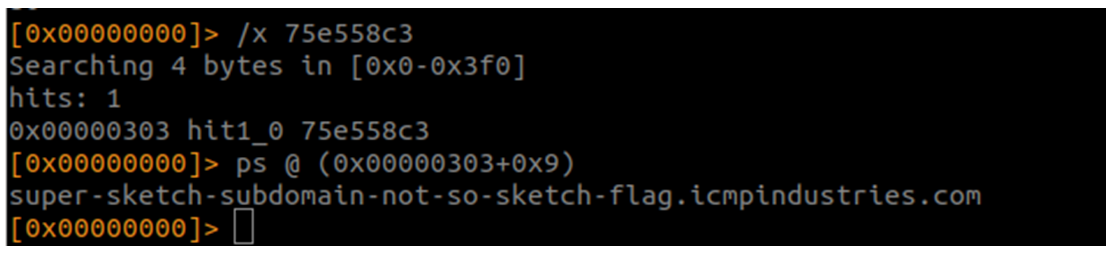
Sólo nos queda la url:
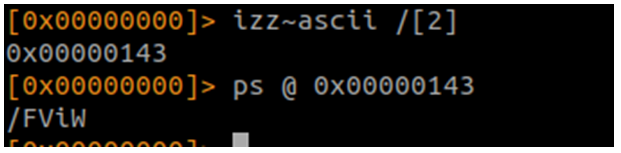
Ya estaría todo lo necesario para obtener los datos de forma automática. Primero vamos a los de la shellcode, a dejarlo bonito:
Script en Python para obtener los datos de las shellcode de Cobalt Strike:
# -*- coding: utf-8 -*-
import r2pipe
import re
import sys
import os
wininetx32 = []
wininetx64 = ['0x000000d7']
def use():
print "Cobalt Strike Shellcode configuration x(32|64) with Radare2 and r2pipe - by Rafa"
print "Use: \"" + sys.argv[0] + "\" \"<shellcode_x64.bin>\""
sys.exit(1)
def printerror(scfile):
print "The file \"" + scfile + "\" is not a Cobalt Strike Shellcode x(32/64)"
def isipaddress(my_ip):
is_valid = re.match("^(([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\.){3}([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])$", my_ip)
if is_valid:
return True
else:
return False
def isdomain(my_hostname):
is_valid = re.match("^(([a-zA-Z]|[a-zA-Z][a-zA-Z0-9\-]*[a-zA-Z0-9])\.)*([A-Za-z]|[A-Za-z][A-Za-z0-9\-]*[A-Za-z0-9])$", my_hostname)
if is_valid:
return True
else:
return False
def isurl(my_url):
is_valid = re.match("^(/(\w+))", my_url)
if is_valid:
return True
else:
return False
def getwininet(arch):
if arch == 'x64':
wininet = r2.cmd("izz~wininet[2]").split('\n')[0]
good = '0x000000d7'
if wininet == good:
return True
else:
return False
else:
wininet1 = r2.cmd("izz~hnet[6]").split('\n')[0]
wininet2 = r2.cmd("izz~hwini[6]").split('\n')[0]
good1 = 'hnet'
good2 = 'hwini'
if ((good1 in wininet1) and (good2 in wininet2)):
return True
else:
return False
def getmagic():
magic = r2.cmd("p8 8").split('\n')[0]
goodx64 = '4883e4f0e8c800'
goodx32 = 'e8890000006089'
if goodx64 in magic:
return 'x64'
elif goodx32 in magic:
return 'x32'
else:
return ''
def getuseragent(arch):
if arch == 'x64':
useragent = r2.cmd("ps @ 0x000001f9")
good = 'User-Agent:'
if good in useragent:
return useragent.replace('\\x0d','')
else:
return ''
else:
finduseragent = r2.cmd("izz~User-Agent:[2]").split('\n')[0]
if finduseragent != '':
useragent = r2.cmd("ps @ "+finduseragent)
good = 'User-Agent:'
if good in useragent:
return useragent.replace('\\x0d','')
else:
return ''
else:
return ''
def getipordomain(arch):
if arch == 'x64':
ipordomain = r2.cmd("ps @ 0x0000038d").split('\n')[0]
if ((isipaddress(ipordomain) == True) or (isdomain(ipordomain) == True)):
return ipordomain
else:
return ''
else:
findipordomain = r2.cmd("/x fdffff")
ipordomaindir = ''
for i in findipordomain.split('\n'):
if 'fdffff' in i:
ipordomaindir = i.split(' ')[0]
break
if ipordomaindir != '':
ipordomain = r2.cmd("ps @ ("+ipordomaindir+"+0x3)").split('\n')[0]
if ((isipaddress(ipordomain) == True) or (isdomain(ipordomain) == True)):
return ipordomain
else:
return ''
else:
return ''
def geturl(arch):
if arch == 'x64':
url = r2.cmd("ps @ 0x000001a9").split('\n')[0]
if (isurl(url) == True):
return url
else:
return ''
else:
findurl = r2.cmd("izz~ascii /[2]").split('\n')[0]
if findurl != '':
url = r2.cmd("ps @ "+findurl).split('\n')[0]
if (isurl(url) == True):
return url
else:
return ''
else:
return ''
def getport(arch):
if arch == 'x64':
porta = r2.cmd("p8 1 @0x113").split('\n')[0]
portb = r2.cmd("p8 1 @0x112").split('\n')[0]
port = r2.cmd("? 0x"+porta+portb+"~^int32[1]").split('\n')[0]
try:
if 1 <= int(port) <= 65535:
return port
else:
return ''
except:
return ''
else:
findport=r2.cmd("izz~WWWWWh[2]").split('\n')[0]
if findport != '':
porta = r2.cmd("p8 1 @ ("+findport+"+0x1c)").split('\n')[0]
portb = r2.cmd("p8 1 @ ("+findport+"+0x1b)").split('\n')[0]
port = r2.cmd("? 0x"+porta+portb+"~^int32[1]").split('\n')[0]
try:
if 1 <= int(port) <= 65535:
return port
else:
return ''
except:
return ''
else:
return ''
if len(sys.argv) != 2:
print ("You need an argument to filename")
sys.exit(1)
path = sys.argv[1]
if os.path.exists(path):
path = sys.argv[1]
r2=r2pipe.open(path)
peformat = r2.cmd("i~format[1]").split('\n')[0]
if peformat not in ('any'):
printerror(path)
use()
myarch = getmagic()
if myarch == '':
printerror(path)
use()
if getwininet(myarch) == False:
printerror(path)
use()
myuseragent = getuseragent(myarch)
if myuseragent == '':
printerror(path)
use()
ipordomain = getipordomain(myarch)
if ipordomain == '':
printerror(path)
use()
myurl = geturl(myarch)
if myurl == '':
printerror(path)
use()
myport = getport(myarch)
if myport == '':
printerror(path)
use()
print ('[*] Shellcode Architecture: %s' % (myarch))
print ('[*] Result: http[s]://%s:%s%s' % (ipordomain,myport,myurl))
print ('[*] IP or domain: %s' % ipordomain)
print ('[*] Port: %s' % myport)
print ('[*] URL: %s' % myurl)
else:
print "The file \"" + path + "\" not exists!"
use()
Esto para el shellcode, pero ¿a que estaría bien sacarlo directamente del artefacto?
Script en Python para extraer el shellcode de los artefactos de Cobalt Strike:
# -*- coding: utf-8 -*-
#!/usr/bin/python
import pefile
import sys
import os
import re
import r2pipe
import hashlib
wininetx32 = []
wininetx64 = ['0x000000d7']
def use():
print "Cobalt Strike Shellcode extractor from Artifacts x(32|64) with pefile, Radare2 and r2pipe - by Rafa"
print "Use: \"" + sys.argv[0] + "\" \"<artifacts.bin>\""
sys.exit(1)
def printerror(scfile):
print "The file \"" + scfile + "\" is not a Cobalt Strike Shellcode x(32/64)"
def decode(data):
decoded = bytearray()
cont = 20
for i in range(20, len(data)):
dec_val = data[((cont - 12))] ^ data[i]
decoded.append(dec_val)
cont = cont + 1
if cont == 24:
cont = 20
return decoded
def imphash(fname):
pe=pefile.PE(fname)
return "%s" % (pe.get_imphash())
def sha256sumfromfile(filepath):
resp = ''
if os.path.exists(filepath):
filename = filepath
sha256_hash = hashlib.sha256()
with open(filename,"rb") as f:
for byte_block in iter(lambda: f.read(4096),b""):
sha256_hash.update(byte_block)
sha256sum = sha256_hash.hexdigest()
if len(sha256sum) == 64:
resp = sha256sum
return resp
def isipaddress(my_ip):
is_valid = re.match("^(([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\.){3}([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])$", my_ip)
if is_valid:
return True
else:
return False
def isdomain(my_hostname):
is_valid = re.match("^(([a-zA-Z]|[a-zA-Z][a-zA-Z0-9\-]*[a-zA-Z0-9])\.)*([A-Za-z]|[A-Za-z][A-Za-z0-9\-]*[A-Za-z0-9])$", my_hostname)
if is_valid:
return True
else:
return False
def isurl(my_url):
is_valid = re.match("^(/(\w+))", my_url)
if is_valid:
return True
else:
return False
def getwininet(arch):
if arch == 'x64':
wininet = r2.cmd("izz~wininet[2]").split('\n')[0]
good = '0x000000d7'
if wininet == good:
return True
else:
return False
else:
wininet1 = r2.cmd("izz~hnet[6]").split('\n')[0]
wininet2 = r2.cmd("izz~hwini[6]").split('\n')[0]
good1 = 'hnet'
good2 = 'hwini'
if ((good1 in wininet1) and (good2 in wininet2)):
return True
else:
return False
def getmagic():
magic = r2.cmd("p8 8").split('\n')[0]
goodx64 = 'e4f0e8c800'
goodx32 = '6089'
if goodx64 in magic:
return 'x64'
elif goodx32 in magic:
return 'x32'
else:
return ''
def getuseragent(arch):
if arch == 'x64':
useragent = r2.cmd("ps @ 0x000001f9")
good = 'User-Agent:'
if good in useragent:
return useragent.replace('\\x0d','')
else:
return ''
else:
finduseragent = r2.cmd("izz~User-Agent:[2]").split('\n')[0]
if finduseragent != '':
useragent = r2.cmd("ps @ "+finduseragent)
good = 'User-Agent:'
if good in useragent:
return useragent.replace('\\x0d','')
else:
return ''
else:
finduseragent = r2.cmd("izz~Mozilla[2]").split('\n')[0]
if finduseragent != '':
useragent = r2.cmd("ps @ "+finduseragent)
good = 'Mozilla'
if good in useragent:
return useragent.replace('\\x0d','')
else:
return ''
else:
return ''
def getipordomain(arch):
if arch == 'x64':
ipordomain = r2.cmd("ps @ 0x0000038d").split('\n')[0]
if ((isipaddress(ipordomain) == True) or (isdomain(ipordomain) == True)):
return ipordomain
else:
return ''
else:
findipordomain = r2.cmd("/x 75e558c3")
ipordomaindir = ''
for i in findipordomain.split('\n'):
if '75e558c3' in i:
ipordomaindir = i.split(' ')[0]
break
if ipordomaindir != '':
ipordomain = r2.cmd("ps @ ("+ipordomaindir+"+0x9)").split('\n')[0]
if ((isipaddress(ipordomain) == True) or (isdomain(ipordomain) == True)):
return ipordomain
else:
return ''
else:
return ''
def geturl(arch):
if arch == 'x64':
url = r2.cmd("ps @ 0x000001a9").split('\n')[0]
if (isurl(url) == True):
return url
else:
return ''
else:
findurl = r2.cmd("izz~ascii /[2]").split('\n')[0]
if findurl != '':
url = r2.cmd("ps @ "+findurl).split('\n')[0]
if (isurl(url) == True):
return url
else:
return ''
else:
return ''
def getport(arch):
if arch == 'x64':
porta = r2.cmd("p8 1 @0x113").split('\n')[0]
portb = r2.cmd("p8 1 @0x112").split('\n')[0]
port = r2.cmd("? 0x"+porta+portb+"~^int32[1]").split('\n')[0]
try:
if 1 <= int(port) <= 65535:
return port
else:
return ''
except:
return ''
else:
findport = r2.cmd("/x 03515168")
portinfindport = ''
for i in findport.split('\n'):
if '03515168' in i:
portinfindport = i.split(' ')[0]
break
if portinfindport != '':
porta = r2.cmd("p8 1 @ ("+portinfindport+"+0x5)").split('\n')[0]
portb = r2.cmd("p8 1 @ ("+portinfindport+"+0x4)").split('\n')[0]
port = r2.cmd("? 0x"+porta+portb+"~^int32[1]").split('\n')[0]
try:
if 1 <= int(port) <= 65535:
return port
else:
return ''
except:
return ''
else:
return ''
if __name__ == "__main__":
if len(sys.argv) != 2:
print >>sys.stderr, "Usage: %s <artifact.exe> - Give me IOCs Cobalt Strike Artifact, by Rafa" % sys.argv[0]
sys.exit(1)
filename = sys.argv[1]
if not os.path.exists(filename):
print >>sys.stderr, "'%s' does not exist" % filename
sys.exit(1)
try:
if imphash(filename) == "dc25ee78e2ef4d36faa0badf1e7461c9":
sha256sum = sha256sumfromfile(filename)
f = open(filename, "rb")
f.seek(0x2200)
shellcode = f.read(0x2600 - 0x2200)
f.close()
data = bytearray(shellcode)
decoded = decode(data)
if decoded:
file_location = filename
file_name = os.path.basename(file_location )
scfilename = 'shellcode_extracted_'+file_name
else:
sys.exit(1)
f = open(scfilename, "wb")
f.write(b'\xFC\xE8\x89\x00' + decoded)
f.close()
r2=r2pipe.open(scfilename)
peformat = r2.cmd("i~format[1]").split('\n')[0]
if peformat not in ('any'):
printerror(scfilename)
print "peformat error"
use()
myarch = getmagic()
if myarch == '':
printerror(scfilename)
print "myarch error"
use()
if getwininet(myarch) == False:
printerror(scfilename)
print "getwininet error"
use()
myuseragent = getuseragent(myarch)
if myuseragent == '':
print printerror(scfilename)
print "myuseragent error"
use()
ipordomain = getipordomain(myarch)
if ipordomain == '':
print printerror(scfilename)
print "ipordomain error"
use()
myurl = geturl(myarch)
if myurl == '':
print printerror(scfilename)
print "myurl error"
use()
myport = getport(myarch)
if myport == '':
print printerror(scfilename)
print "myport error"
use()
print ('[*] Filename: %s' % (filename))
print ('[*] Sha256sum: %s' % (sha256sum))
print ('[*] Shellcode Architecture: %s' % (myarch))
print ('[*] Result: http[s]://%s:%s%s' % (ipordomain,myport,myurl))
print ('[*] IP or domain: %s' % ipordomain)
print ('[*] Port: %s' % myport)
print ('[*] URL: %s' % myurl)
print ('[*] Header: %s' % myuseragent)
except Exception, msg:
print "[!] error: %s" % msg
Veamos el resultado:
[*] Filename: ./00641d85e6cb840f92c630ae0cfecd00e70e2efb16ed8b8a1bd026bdeebb56c0_artifact.exe
[*] Sha256sum: 00641d85e6cb840f92c630ae0cfecd00e70e2efb16ed8b8a1bd026bdeebb56c0
[*] Shellcode Architecture: x32
[*] Result: http[s]://cs1.investe.co.uk:443/tRc3
[*] IP or domain: cs1.investe.co.uk
[*] Port: 443
[*] URL: /tRc3
[*] Header: User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; .NET CLR 2.0.50727; 360space)
[*] Filename: ./06f8004835c5851529403f73ad23168b1127315d02c68e0153e362a73f915c72_artifact.exe
[*] Sha256sum: 06f8004835c5851529403f73ad23168b1127315d02c68e0153e362a73f915c72
[*] Shellcode Architecture: x32
[*] Result: http[s]://72.14.184.90:443/Search/News/
[*] IP or domain: 72.14.184.90
[*] Port: 443
[*] URL: /Search/News/
[*] Header: User-Agent: Mozilla/5.0 (compatible, MSIE 11, Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./07f1888b3febc5971660147d4c6c3ad1c8fda262a797c8bff375ad6f0704413d_artifact.exe
[*] Sha256sum: 07f1888b3febc5971660147d4c6c3ad1c8fda262a797c8bff375ad6f0704413d
[*] Shellcode Architecture: x32
[*] Result: http[s]://37.139.6.92:80/kuK1
[*] IP or domain: 37.139.6.92
[*] Port: 80
[*] URL: /kuK1
[*] Header: User-Agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.2; WOW64; Trident/6.0; MDDCJS)
[*] Filename: ./0e36be5524820cedba0ecd76131158d0317f760f51b8174ff381ef16365696c7_artifact.exe
[*] Sha256sum: 0e36be5524820cedba0ecd76131158d0317f760f51b8174ff381ef16365696c7
[*] Shellcode Architecture: x32
[*] Result: http[s]://82.196.0.186:80/XiZA
[*] IP or domain: 82.196.0.186
[*] Port: 80
[*] URL: /XiZA
[*] Header: User-Agent: Mozilla/5.0 (compatible, MSIE 11, Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./10cb3101476923121269b245367c7c71a98c736f649395dbd15693c8d0effe08_artifact.exe
[*] Sha256sum: 10cb3101476923121269b245367c7c71a98c736f649395dbd15693c8d0effe08
[*] Shellcode Architecture: x32
[*] Result: http[s]://portal.jsetrader.co.za:443/posts/32251817/ivc/7600
[*] IP or domain: portal.jsetrader.co.za
[*] Port: 443
[*] URL: /posts/32251817/ivc/7600
[*] Header: Host: stackoverflow[.]com
Accept: */*
Accept-Language: en-US,en;q=0.5
X-Requested-With: XMLHTTPRequest
Etag: 4aeebe4a839401711e5daeaaa0fe85d5
Connection: close
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.
[*] Filename: ./1cc92fca43c469507fb343d066e9cf81c8ae318276b41d5f3cf1e2f76e1daa5d_artifact.exe
[*] Sha256sum: 1cc92fca43c469507fb343d066e9cf81c8ae318276b41d5f3cf1e2f76e1daa5d
[*] Shellcode Architecture: x32
[*] Result: http[s]://104.236.184.25:443/mail?dfs=update
[*] IP or domain: 104.236.184.25
[*] Port: 443
[*] URL: /mail?dfs=update
[*] Header: x-D-A: a1j3==
User-Agent: Mozilla/5.0 (Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./1df6465b13e110ff7501683c7481e625cf9201e1dacdc36288a17bfd4058181c_artifact.exe
[*] Sha256sum: 1df6465b13e110ff7501683c7481e625cf9201e1dacdc36288a17bfd4058181c
[*] Shellcode Architecture: x32
[*] Result: http[s]://82.145.59.79:443/Gdz7
[*] IP or domain: 82.145.59.79
[*] Port: 443
[*] URL: /Gdz7
[*] Header: User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0)
[*] Filename: ./1f2ea18e34d8bcf435eb6f571b9ae2182675ae6357d282679ef669797aa6f38b_artifact.exe
[*] Sha256sum: 1f2ea18e34d8bcf435eb6f571b9ae2182675ae6357d282679ef669797aa6f38b
[*] Shellcode Architecture: x32
[*] Result: http[s]://143.108.233.233:80/AdnI
[*] IP or domain: 143.108.233.233
[*] Port: 80
[*] URL: /AdnI
[*] Header: User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; SV1; .NET CLR 2.0.50727)
[*] Filename: ./2d12f7359ea4dcaa0ab7c1090e84a2bd48cfa6bab4cee641adb504bfcd1f3b9b_artifact.exe
[*] Sha256sum: 2d12f7359ea4dcaa0ab7c1090e84a2bd48cfa6bab4cee641adb504bfcd1f3b9b
[*] Shellcode Architecture: x32
[*] Result: http[s]://download.instagarm[.]com:8080/5mKo
[*] IP or domain: download.instagarm[.]com
[*] Port: 8080
[*] URL: /5mKo
[*] Header: User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; .NET CLR 2.0.50727; 360space)
[*] Filename: ./30d197817fb19ee3a39d9ff8246c731c3b8c543f8c6ef387eb2ff7e9c581adf6_artifact.exe
[*] Sha256sum: 30d197817fb19ee3a39d9ff8246c731c3b8c543f8c6ef387eb2ff7e9c581adf6
[*] Shellcode Architecture: x32
[*] Result: http[s]://wideopensea[.]com:443/6x4z
[*] IP or domain: wideopensea[.]com
[*] Port: 443
[*] URL: /6x4z
[*] Header: Content-Type: application/json; charset=utf-8
Referer: http://www.msn[.]com/?pc=teamserver&cid=UE01DHP
Origin: http://www.msn[.]com
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./32822d9af524b0d8280f5df0ba5ce8bcab26c2d94cd45b7c360529ae516cf2e3_artifact.exe
[*] Sha256sum: 32822d9af524b0d8280f5df0ba5ce8bcab26c2d94cd45b7c360529ae516cf2e3
[*] Shellcode Architecture: x32
[*] Result: http[s]://185.14.186.94:80/8auN
[*] IP or domain: 185.14.186.94
[*] Port: 80
[*] URL: /8auN
[*] Header: User-Agent: Mozilla/5.0 (compatible, MSIE 11, Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./3bd5f6f088a2668f9d3a8161c961d52417a36b75af5adaf9f1288f7992ebf604_artifact.exe
[*] Sha256sum: 3bd5f6f088a2668f9d3a8161c961d52417a36b75af5adaf9f1288f7992ebf604
[*] Shellcode Architecture: x32
[*] Result: http[s]://185.202.2.182:2525/jNp4
[*] IP or domain: 185.202.2.182
[*] Port: 2525
[*] URL: /jNp4
[*] Header: User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.0; Trident/5.0; BOIE9;ENUSMSNIP)
[*] Filename: ./43df13e176eb083a6af986fc75bf37985ead4053c9b128fa27285a2e5f306c59_artifact.exe
[*] Sha256sum: 43df13e176eb083a6af986fc75bf37985ead4053c9b128fa27285a2e5f306c59
[*] Shellcode Architecture: x32
[*] Result: http[s]://18.221.162.53:80/biIH
[*] IP or domain: 18.221.162.53
[*] Port: 80
[*] URL: /biIH
[*] Header: User-Agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.2; Win64; x64; Trident/6.0)
[*] Filename: ./4873a1f74b1245009c083b0fb90900d4ed01a5c651b3ed9c2e716e61ba5079be_artifact.exe
[*] Sha256sum: 4873a1f74b1245009c083b0fb90900d4ed01a5c651b3ed9c2e716e61ba5079be
[*] Shellcode Architecture: x32
[*] Result: http[s]://80.245.106.109:80/2oMn
[*] IP or domain: 80.245.106.109
[*] Port: 80
[*] URL: /2oMn
[*] Header: User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0)
[*] Filename: ./4a045d9205935a73d7d9b3b6e961fc1e5b3516d380a5ea28d3f0a8f576d6439b_artifact.exe
[*] Sha256sum: 4a045d9205935a73d7d9b3b6e961fc1e5b3516d380a5ea28d3f0a8f576d6439b
[*] Shellcode Architecture: x32
[*] Result: http[s]://10.128.20.82:443/o3Mm
[*] IP or domain: 10.128.20.82
[*] Port: 443
[*] URL: /o3Mm
[*] Header: User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./4bd09b224117790ac61c8dbe039df1e3a0548626887b7b06d1abff0101e3d989_artifact.exe
[*] Sha256sum: 4bd09b224117790ac61c8dbe039df1e3a0548626887b7b06d1abff0101e3d989
[*] Shellcode Architecture: x32
[*] Result: http[s]://82.196.6.218:80/PCzO
[*] IP or domain: 82.196.6.218
[*] Port: 80
[*] URL: /PCzO
[*] Header: User-Agent: Mozilla/5.0 (compatible, MSIE 11, Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./4e16d2e29f1ebc947cbf6b985cf7a9a46ec85c7e80f134f91fa063ed87575b30_artifact.exe
[*] Sha256sum: 4e16d2e29f1ebc947cbf6b985cf7a9a46ec85c7e80f134f91fa063ed87575b30
[*] Shellcode Architecture: x32
[*] Result: http[s]://62.31.181.67:443/pHZJ
[*] IP or domain: 62.31.181.67
[*] Port: 443
[*] URL: /pHZJ
[*] Header: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0)
[*] Filename: ./56861f8382d10a3d50ea0571eb44d8b04da84931166a9a5707fdbc1cf60035b3_artifact.exe
[*] Sha256sum: 56861f8382d10a3d50ea0571eb44d8b04da84931166a9a5707fdbc1cf60035b3
[*] Shellcode Architecture: x32
[*] Result: http[s]://www.tarponcoastbank[.]com:443/Ww8V
[*] IP or domain: www.tarponcoastbank[.]com
[*] Port: 443
[*] URL: /Ww8V
[*] Header: User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./6043c45ca9038e45457bb13133109d647417776cd57b75468821f2b68d190a1c_artifact.exe
[*] Sha256sum: 6043c45ca9038e45457bb13133109d647417776cd57b75468821f2b68d190a1c
[*] Shellcode Architecture: x32
[*] Result: http[s]://104.248.41.209:80/m9lJ
[*] IP or domain: 104.248.41.209
[*] Port: 80
[*] URL: /m9lJ
[*] Header: User-Agent: Mozilla/5.0 (compatible, MSIE 11, Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./61ffe0a4549a36746a342b3bb75f0b0d2964cc6e15a4597fa7c34e3ca6065d76_artifact.exe
[*] Sha256sum: 61ffe0a4549a36746a342b3bb75f0b0d2964cc6e15a4597fa7c34e3ca6065d76
[*] Shellcode Architecture: x32
[*] Result: http[s]://37.139.26.119:80/1zKf
[*] IP or domain: 37.139.26.119
[*] Port: 80
[*] URL: /1zKf
[*] Header: User-Agent: Mozilla/5.0 (compatible, MSIE 11, Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./6496905d4e7677f0a80dac27722ce8fddd18256830d44f4d13709d7978626f49_artifact.exe
[*] Sha256sum: 6496905d4e7677f0a80dac27722ce8fddd18256830d44f4d13709d7978626f49
[*] Shellcode Architecture: x32
[*] Result: http[s]://go0gIe[.]com:80/8fEy
[*] IP or domain: go0gIe[.]com
[*] Port: 80
[*] URL: /8fEy
[*] Header: User-Agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.2; Win64; x64; Trident/6.0; MATMJS)
[*] Filename: ./6c762972cf95bf6da96fe64c3a335756aedb871060af90eb6bd87fc683f6492c_artifact.exe
[*] Sha256sum: 6c762972cf95bf6da96fe64c3a335756aedb871060af90eb6bd87fc683f6492c
[*] Shellcode Architecture: x32
[*] Result: http[s]://bingstatistics.azureedge.net:443/en-us
[*] IP or domain: bingstatistics.azureedge.net
[*] Port: 443
[*] URL: /en-us
[*] Header: Host: bingstatistics.azureedge.net
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.1; Trident/4.0)
[*] Filename: ./6dda09c3d2078caefb228a74ec4172eeb4552ea10a9a849d3060c68d4d2657bd_artifact.exe
[*] Sha256sum: 6dda09c3d2078caefb228a74ec4172eeb4552ea10a9a849d3060c68d4d2657bd
[*] Shellcode Architecture: x32
[*] Result: http[s]://windowsupdate.ex:80/eXAv
[*] IP or domain: windowsupdate.ex
[*] Port: 80
[*] URL: /eXAv
[*] Header: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0)
[*] Filename: ./6eb1b9271c95edc0c095c50777bfabdc15f543a9295222760a8c9e124f096a41_artifact.exe
[*] Sha256sum: 6eb1b9271c95edc0c095c50777bfabdc15f543a9295222760a8c9e124f096a41
[*] Shellcode Architecture: x32
[*] Result: http[s]://192.168.50.113:80/PjJX
[*] IP or domain: 192.168.50.113
[*] Port: 80
[*] URL: /PjJX
[*] Header: User-Agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.2; WOW64; Trident/6.0; MDDCJS)
[*] Filename: ./7166c84bb35b94a497851bffefe7cce60788e9bccbbf550cd162ec8ddc0c9266_artifact.exe
[*] Sha256sum: 7166c84bb35b94a497851bffefe7cce60788e9bccbbf550cd162ec8ddc0c9266
[*] Shellcode Architecture: x32
[*] Result: http[s]://37.139.31.50:80/1vEp
[*] IP or domain: 37.139.31.50
[*] Port: 80
[*] URL: /1vEp
[*] Header: User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0; NP06)
[*] Filename: ./72c179e143cb25e8f78e6bd3d116deca1db3b97db93db521a6a60503103857bf_artifact.exe
[*] Sha256sum: 72c179e143cb25e8f78e6bd3d116deca1db3b97db93db521a6a60503103857bf
[*] Shellcode Architecture: x32
[*] Result: http[s]://d3iq1ap6go3fkx.cloudfront.net:443/56yx
[*] IP or domain: d3iq1ap6go3fkx.cloudfront.net
[*] Port: 443
[*] URL: /56yx
[*] Header: User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:50.0) Gecko/20100101 Firefox/50.0
[*] Filename: ./7a1602e83f42292c7630b3914cf391bfd49f7e3f641288d3446a4b015785d321_artifact.exe
[*] Sha256sum: 7a1602e83f42292c7630b3914cf391bfd49f7e3f641288d3446a4b015785d321
[*] Shellcode Architecture: x32
[*] Result: http[s]://icmpindustries[.]com:80/8Sbo
[*] IP or domain: icmpindustries[.]com
[*] Port: 80
[*] URL: /8Sbo
[*] Header: User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:50.0) Gecko/20100101 Firefox/50.0
[*] Filename: ./7d6384399f121e1295243ea82f3422c6f46c619f5777bb4e5c34152e1a4b5bef_artifact.exe
[*] Sha256sum: 7d6384399f121e1295243ea82f3422c6f46c619f5777bb4e5c34152e1a4b5bef
[*] Shellcode Architecture: x32
[*] Result: http[s]://165.22.67.12:80/OGVp
[*] IP or domain: 165.22.67.12
[*] Port: 80
[*] URL: /OGVp
[*] Header: User-Agent: Mozilla/5.0 (compatible, MSIE 11, Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./809cad4ddd921f0bbdcaa267dd6fb5d2528730c5d55df773846dc7b63643ba6c_artifact.exe
[*] Sha256sum: 809cad4ddd921f0bbdcaa267dd6fb5d2528730c5d55df773846dc7b63643ba6c
[*] Shellcode Architecture: x32
[*] Result: http[s]://104.236.184.25:443/mail?dfs=update
[*] IP or domain: 104.236.184.25
[*] Port: 443
[*] URL: /mail?dfs=update
[*] Header: x-D-A: a1j3==
User-Agent: Mozilla/5.0 (Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./85a1659c7ba9ded0c1b84b34b505f48237d495d0179c28f6c1d5a95bd87064d8_artifact.exe
[*] Sha256sum: 85a1659c7ba9ded0c1b84b34b505f48237d495d0179c28f6c1d5a95bd87064d8
[*] Shellcode Architecture: x32
[*] Result: http[s]://165.22.71.187:80/Hb8z
[*] IP or domain: 165.22.71.187
[*] Port: 80
[*] URL: /Hb8z
[*] Header: User-Agent: Mozilla/5.0 (compatible, MSIE 11, Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./8880ae12848d889ac6e527e1bbd412248ea33d6da3545e4bc062ea8b29863516_artifact.exe
[*] Sha256sum: 8880ae12848d889ac6e527e1bbd412248ea33d6da3545e4bc062ea8b29863516
[*] Shellcode Architecture: x32
[*] Result: http[s]://188.166.105.24:80/jH2x
[*] IP or domain: 188.166.105.24
[*] Port: 80
[*] URL: /jH2x
[*] Header: User-Agent: Mozilla/5.0 (compatible, MSIE 11, Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./917632c0529845fb50248729b04accd55ab00dfc142b5750a73c145eb1aea3e8_artifact.exe
[*] Sha256sum: 917632c0529845fb50248729b04accd55ab00dfc142b5750a73c145eb1aea3e8
[*] Shellcode Architecture: x32
[*] Result: http[s]://217.8.117.37:80/iEjD
[*] IP or domain: 217.8.117.37
[*] Port: 80
[*] URL: /iEjD
[*] Header: User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0; MASP)
[*] Filename: ./9675f832a7dfda9e5cbbc6ae409b8d630392e56c29fe4e110d27134100e31d52_artifact.exe
[*] Sha256sum: 9675f832a7dfda9e5cbbc6ae409b8d630392e56c29fe4e110d27134100e31d52
[*] Shellcode Architecture: x32
[*] Result: http[s]://5.79.119.191:8080/1dzM
[*] IP or domain: 5.79.119.191
[*] Port: 8080
[*] URL: /1dzM
[*] Header: User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0)
[*] Filename: ./9972402dcc080a826c0010948d8c32ab4fce83c13d30e3e2eb074d4c31a2b9af_artifact.exe
[*] Sha256sum: 9972402dcc080a826c0010948d8c32ab4fce83c13d30e3e2eb074d4c31a2b9af
[*] Shellcode Architecture: x32
[*] Result: http[s]://go0gIe[.]com:80/XYv5
[*] IP or domain: go0gIe[.]com
[*] Port: 80
[*] URL: /XYv5
[*] Header: User-Agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.2; Win64; x64; Trident/6.0; MATMJS)
[*] Filename: ./9a0aeaeae4483c51d51428ec32800e37d7c9de4b51d7f3e7f7f63cec59d77584_artifact.exe
[*] Sha256sum: 9a0aeaeae4483c51d51428ec32800e37d7c9de4b51d7f3e7f7f63cec59d77584
[*] Shellcode Architecture: x32
[*] Result: http[s]://192.168.1.50:4444/OHuP
[*] IP or domain: 192.168.1.50
[*] Port: 4444
[*] URL: /OHuP
[*] Header: User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0; InfoPath.2; .NET4.0C; .NET4.0E)
[*] Filename: ./9a0c4694d4ad3fd8917149bf2cf1baf4b2d37532b5b02cdca14356277c931039_artifact.exe
[*] Sha256sum: 9a0c4694d4ad3fd8917149bf2cf1baf4b2d37532b5b02cdca14356277c931039
[*] Shellcode Architecture: x32
[*] Result: http[s]://178.128.230.240:80/Sj9f
[*] IP or domain: 178.128.230.240
[*] Port: 80
[*] URL: /Sj9f
[*] Header: User-Agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.2; Trident/6.0; Touch)
[*] Filename: ./9a42eca4df1bb5dfe0b7d2c2b28e10e88a0c35d881ad20f162174f9bb579c197_artifact.exe
[*] Sha256sum: 9a42eca4df1bb5dfe0b7d2c2b28e10e88a0c35d881ad20f162174f9bb579c197
[*] Shellcode Architecture: x32
[*] Result: http[s]://82.196.0.186:80/bFIk
[*] IP or domain: 82.196.0.186
[*] Port: 80
[*] URL: /bFIk
[*] Header: User-Agent: Mozilla/5.0 (compatible, MSIE 11, Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./9a8548f1797803a6a29f128a141dcf93d0333e1203774ecbdc295a6b072ee77b_artifact.exe
[*] Sha256sum: 9a8548f1797803a6a29f128a141dcf93d0333e1203774ecbdc295a6b072ee77b
[*] Shellcode Architecture: x32
[*] Result: http[s]://37.139.4.53:80/QZhI
[*] IP or domain: 37.139.4.53
[*] Port: 80
[*] URL: /QZhI
[*] Header: User-Agent: Mozilla/5.0 (compatible, MSIE 11, Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./a0cfec815cb74a7671265fd5e0790a2a79c05fe0ef16d2d0c87584049d06658b_artifact.exe
[*] Sha256sum: a0cfec815cb74a7671265fd5e0790a2a79c05fe0ef16d2d0c87584049d06658b
[*] Shellcode Architecture: x32
[*] Result: http[s]://192.168.1.120:4443/i6rK
[*] IP or domain: 192.168.1.120
[*] Port: 4443
[*] URL: /i6rK
[*] Header: User-Agent: Mozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.2; WOW64; Trident/6.0; BOIE9;ENUS)
[*] Filename: ./a0e76ae8143c4e8605cd95b80f4f13b9099889925b35b79a872d66f9bac0c8ff_artifact.exe
[*] Sha256sum: a0e76ae8143c4e8605cd95b80f4f13b9099889925b35b79a872d66f9bac0c8ff
[*] Shellcode Architecture: x32
[*] Result: http[s]://173.230.133.135:443/aEiM
[*] IP or domain: 173.230.133.135
[*] Port: 443
[*] URL: /aEiM
[*] Header: User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.0; WOW64; Trident/5.0; msn OptimizedIE8;ENUS)
[*] Filename: ./a94d39f150647a226e3f3952cdfc4906a9049f75379a467e908db6707a61907f_artifact.exe
[*] Sha256sum: a94d39f150647a226e3f3952cdfc4906a9049f75379a467e908db6707a61907f
[*] Shellcode Architecture: x32
[*] Result: http[s]://ajax.microsoft[.]com:443/en-us
[*] IP or domain: ajax.microsoft[.]com
[*] Port: 443
[*] URL: /en-us
[*] Header: Host: defender.azureedge.net
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0; MAAU; NP08)
[*] Filename: ./ab4c3289480dedf8cae5201845d6023053aaf10d22772104e0b240aaf2a022d3_artifact.exe
[*] Sha256sum: ab4c3289480dedf8cae5201845d6023053aaf10d22772104e0b240aaf2a022d3
[*] Shellcode Architecture: x32
[*] Result: http[s]://23.97.178.173:8080/RadE
[*] IP or domain: 23.97.178.173
[*] Port: 8080
[*] URL: /RadE
[*] Header: User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; .NET CLR 2.0.50727; 360space)
[*] Filename: ./b894ae0ec3b677692b9f78ca1492b012f0a38be98e6e0eb6c67077c2b3e92cb4_artifact.exe
[*] Sha256sum: b894ae0ec3b677692b9f78ca1492b012f0a38be98e6e0eb6c67077c2b3e92cb4
[*] Shellcode Architecture: x32
[*] Result: http[s]://94.100.18.43:8443/x3lE
[*] IP or domain: 94.100.18.43
[*] Port: 8443
[*] URL: /x3lE
[*] Header: User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0; BOIE9;ENXA)
[*] Filename: ./b97b606aef81420a441aba88b42c44aa8e102390434be5714d33bb07645912d2_artifact.exe
[*] Sha256sum: b97b606aef81420a441aba88b42c44aa8e102390434be5714d33bb07645912d2
[*] Shellcode Architecture: x32
[*] Result: http[s]://ec2-18-222-171-22.us-east-2.compute.amazonaws[.]com:80/69wv
[*] IP or domain: ec2-18-222-171-22.us-east-2.compute.amazonaws[.]com
[*] Port: 80
[*] URL: /69wv
[*] Header: User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
[*] Filename: ./bca4d36e65fc970e7a9a44f41037aae025501c0aac578487d62fa719ebe2f295_artifact.exe
[*] Sha256sum: bca4d36e65fc970e7a9a44f41037aae025501c0aac578487d62fa719ebe2f295
[*] Shellcode Architecture: x32
[*] Result: http[s]://35.226.222.43:80/lGw2
[*] IP or domain: 35.226.222.43
[*] Port: 80
[*] URL: /lGw2
[*] Header: User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; .NET CLR 2.0.50727; 360space)
[*] Filename: ./c2d9bbd5163a8e733483bf5d0d4959f053a2307d275b81eb38e69d87f1f5df7e_artifact.exe
[*] Sha256sum: c2d9bbd5163a8e733483bf5d0d4959f053a2307d275b81eb38e69d87f1f5df7e
[*] Shellcode Architecture: x32
[*] Result: http[s]://202.59.79.131:443/h2lV
[*] IP or domain: 202.59.79.131
[*] Port: 443
[*] URL: /h2lV
[*] Header: User-Agent: Mozilla/4.0 (compatible; MSIE 5.0; Windows NT; DigExt; DTS Agent
[*] Filename: ./c4979b7f2d10da7da13a3e6b4688448d919d0a7bb7bc571d58546e99263c3e9c_artifact.exe
[*] Sha256sum: c4979b7f2d10da7da13a3e6b4688448d919d0a7bb7bc571d58546e99263c3e9c
[*] Shellcode Architecture: x32
[*] Result: http[s]://104.248.41.209:80/eWHX
[*] IP or domain: 104.248.41.209
[*] Port: 80
[*] URL: /eWHX
[*] Header: User-Agent: Mozilla/5.0 (compatible, MSIE 11, Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./c5870b786d4a01b27b079bbf2ce6d36eae7c07378c0346e9cd0dde30c699b59c_artifact.exe
[*] Sha256sum: c5870b786d4a01b27b079bbf2ce6d36eae7c07378c0346e9cd0dde30c699b59c
[*] Shellcode Architecture: x32
[*] Result: http[s]://103.68.251.31:443/eJiD
[*] IP or domain: 103.68.251.31
[*] Port: 443
[*] URL: /eJiD
[*] Header: User-Agent: Mozilla/4.0 (compatible; MSIE 7.0b; Windows NT 6.0)
[*] Filename: ./d04e0d4ef5f6dea2b68aad4f688090ec861fd2c158bc94c489e9f9486c9fb4c2_artifact.exe
[*] Sha256sum: d04e0d4ef5f6dea2b68aad4f688090ec861fd2c158bc94c489e9f9486c9fb4c2
[*] Shellcode Architecture: x32
[*] Result: http[s]://10.61.20.120:8081/9Bkv
[*] IP or domain: 10.61.20.120
[*] Port: 8081
[*] URL: /9Bkv
[*] Header: User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./d13a3c54759d69d02a0a4fdeb0bd1977149edc5087073f60cfcb9a0484a1bcd7_artifact.exe
[*] Sha256sum: d13a3c54759d69d02a0a4fdeb0bd1977149edc5087073f60cfcb9a0484a1bcd7
[*] Shellcode Architecture: x32
[*] Result: http[s]://transport2.rail-admin.ml:80/eMUU
[*] IP or domain: transport2.rail-admin.ml
[*] Port: 80
[*] URL: /eMUU
[*] Header: User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; .NET CLR 2.0.50727; 360space)
[*] Filename: ./dbbcb955538dc2fb65f4336f5a5b397d735dc10b20428d9d164a4284856295f4_artifact.exe
[*] Sha256sum: dbbcb955538dc2fb65f4336f5a5b397d735dc10b20428d9d164a4284856295f4
[*] Shellcode Architecture: x32
[*] Result: http[s]://146.185.136.102:80/IDvY
[*] IP or domain: 146.185.136.102
[*] Port: 80
[*] URL: /IDvY
[*] Header: User-Agent: Mozilla/5.0 (compatible, MSIE 11, Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./dd12b3d1f17ec5638aa1f017cb75b649f9dad046406406d7ac00e9d81b2cff63_artifact.exe
[*] Sha256sum: dd12b3d1f17ec5638aa1f017cb75b649f9dad046406406d7ac00e9d81b2cff63
[*] Shellcode Architecture: x32
[*] Result: http[s]://198.211.124.33:80/dOCf
[*] IP or domain: 198.211.124.33
[*] Port: 80
[*] URL: /dOCf
[*] Header: User-Agent: Mozilla/5.0 (compatible, MSIE 11, Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./e3a3f134fbdad25ee4635c5df3d660317bbc71cade0e4dfab71f82cf8cb0dfe0_artifact.exe
[*] Sha256sum: e3a3f134fbdad25ee4635c5df3d660317bbc71cade0e4dfab71f82cf8cb0dfe0
[*] Shellcode Architecture: x32
[*] Result: http[s]://198.211.126.150:80/VLRh
[*] IP or domain: 198.211.126.150
[*] Port: 80
[*] URL: /VLRh
[*] Header: User-Agent: Mozilla/5.0 (compatible, MSIE 11, Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./eb1d75f02e09b08c65e1541bddcd6888c334977bb1fb603fa45dcd1a836bb406_artifact.exe
[*] Sha256sum: eb1d75f02e09b08c65e1541bddcd6888c334977bb1fb603fa45dcd1a836bb406
[*] Shellcode Architecture: x32
[*] Result: http[s]://78.142.18.157:80/nOMR
[*] IP or domain: 78.142.18.157
[*] Port: 80
[*] URL: /nOMR
[*] Header: User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0)
[*] Filename: ./ed4bb84c5625b997bd5cb8bcda272277e1c0c89dc0a2d771931aff7dc6776453_artifact.exe
[*] Sha256sum: ed4bb84c5625b997bd5cb8bcda272277e1c0c89dc0a2d771931aff7dc6776453
[*] Shellcode Architecture: x32
[*] Result: http[s]://104.207.142.100:80/mail?dfs=update
[*] IP or domain: 104.207.142.100
[*] Port: 80
[*] URL: /mail?dfs=update
[*] Header: x-D-A: a1j3==
User-Agent: Mozilla/5.0 (Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./f4d59b65f2b22854a305736005bf68c042355f2b0b4b8609d5b0c9ecc827eacc_artifact.exe
[*] Sha256sum: f4d59b65f2b22854a305736005bf68c042355f2b0b4b8609d5b0c9ecc827eacc
[*] Shellcode Architecture: x32
[*] Result: http[s]://146.185.158.252:80/77zt
[*] IP or domain: 146.185.158.252
[*] Port: 80
[*] URL: /77zt
[*] Header: User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows Phone OS 7.5; Trident/5.0; IEMobile/9.0; LG; LG-E906)
[*] Filename: ./f61d8c2577a766c572d7fed898e88e19656dae5baf0f120b71c6a39432f56adb_artifact.exe
[*] Sha256sum: f61d8c2577a766c572d7fed898e88e19656dae5baf0f120b71c6a39432f56adb
[*] Shellcode Architecture: x32
[*] Result: http[s]://37.139.26.80:80/Odx1
[*] IP or domain: 37.139.26.80
[*] Port: 80
[*] URL: /Odx1
[*] Header: User-Agent: Mozilla/5.0 (compatible, MSIE 11, Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./f956062680e4996a939c4afed522d101ad2da2187bbb2ed9454cf7155e235a65_artifact.exe
[*] Sha256sum: f956062680e4996a939c4afed522d101ad2da2187bbb2ed9454cf7155e235a65
[*] Shellcode Architecture: x32
[*] Result: http[s]://23.253.56.203:80/YdQN
[*] IP or domain: 23.253.56.203
[*] Port: 80
[*] URL: /YdQN
[*] Header: Mozilla/5.0 (Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
[*] Filename: ./f9727ea0ffb9a8581d821a25c01fdde9bffc7b22847573b0b601483fcdabbdbe_artifact.exe
[*] Sha256sum: f9727ea0ffb9a8581d821a25c01fdde9bffc7b22847573b0b601483fcdabbdbe
[*] Shellcode Architecture: x32
[*] Result: http[s]://139.180.219.174:8956/EmiA
[*] IP or domain: 139.180.219.174
[*] Port: 8956
[*] URL: /EmiA
[*] Header: User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0; NP06)
[*] Filename: ./fef6d4f9ed87c5f991660a768772cd8d723e07b4b9861ecc63e47ed69f6c62d1_artifact.exe
[*] Sha256sum: fef6d4f9ed87c5f991660a768772cd8d723e07b4b9861ecc63e47ed69f6c62d1
[*] Shellcode Architecture: x32
[*] Result: http[s]://super-sketch-subdomain-not-so-sketch-flag.icmpindustries[.]com:80/FViW
[*] IP or domain: super-sketch-subdomain-not-so-sketch-flag.icmpindustries[.]com
[*] Port: 80
[*] URL: /FViW
[*] Header: User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:50.0) Gecko/20100101 Firefox/50.0
Para que funcione tenéis que tener instalado radare2, r2pipe y pefile, qué os voy a contar :-D
Me he fijado que el user-agent a veces se corta, será por lo que os comentaba del tamaño inicial de la extracción del shellcode. Con añadirle un tamaño superior, listo.
Espero que os haya gustado!
Hasta otra!